Wenn Sie Fragen zu den Produkten von MEAN WELL haben, lesen Sie bitte zuerst die FAQ. Wenn die aufgeführten Antworten Ihre Probleme immer noch nicht lösen können, wenden Sie sich bitte an unsere lokalen Händler. Diese sollten Ihnen antworten, sobald Sie Ihre Anfrage erhalten haben.
KNX Data Secure
Q1
What is KNX Data Secure?
Ans
KNX Data Secure signs and encrypts the communication telegrams in the KNX network to avoid the manipulation by unauthorized access or hackers.
The secured communication includes commissioning(configuration) processes with the ETS as well as the runtime(daily) communication between devices. The concept ensures that all or only selected KNX telegrams are authenticated and encrypted regardless of the medium.
As result, the communication between sender and receiver can neither be interpreted nor manipulated.

The secured communication includes commissioning(configuration) processes with the ETS as well as the runtime(daily) communication between devices. The concept ensures that all or only selected KNX telegrams are authenticated and encrypted regardless of the medium.
As result, the communication between sender and receiver can neither be interpreted nor manipulated.

Q2
What is the security level used in KNX Data Secure?
Ans
KNX Data Secure standardized according to EN 50090-3-4 which relies on ISO 18033-3 standardized security algorithms such as AES 128-bit encryption. KNX protects against hacker attacks on the digital infrastructure of networked buildings. KNX Data Secure enables secure communication at telegram level from sender to receiver (end-to-end protection).
The system integrators establish a secure communication channel, including authentication of the authorized communication partners and encryption of the transmission during commissioning(configuration) with ETS software.
The system integrators establish a secure communication channel, including authentication of the authorized communication partners and encryption of the transmission during commissioning(configuration) with ETS software.
Q3
Is the KNX telegram different between plain one and Data Secure one?
Ans
KNX Data Secure telegram uses a longer (Extended Frames) format for the transmission of authenticated and encrypted data than plain one. This has no effect on the speed of the devices.
For details, check FAQ “Why KNX Data Secure has same speed as plain one”.
For details, check FAQ “Why KNX Data Secure has same speed as plain one”.
Q4
Can I add Data Secure KNX devices into existing traditional KNX installation?
Ans
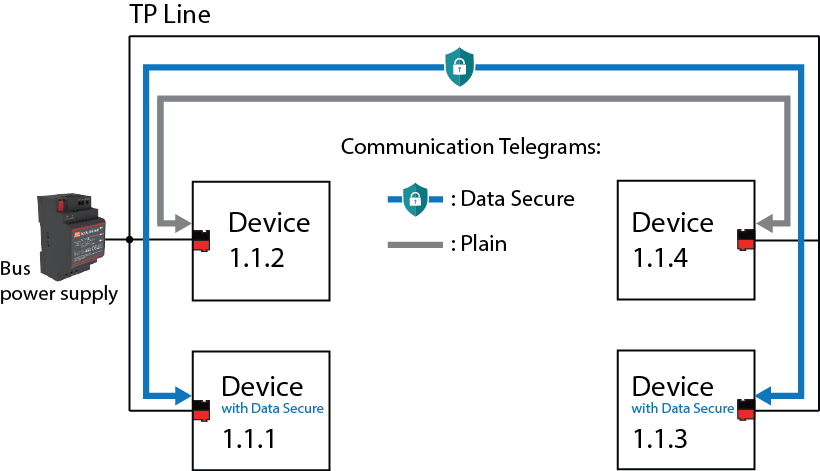
Yes, it is possible to upgrade some parts of existing installation with new KNX Data Secure devices.
Furthermore, it can also have mixed operation of Secure and plain(conventional) communication on a sensor or actuator via different communication objects.
However, secured and unsecured communication via one and the same communication object is not possible. The ETS project determines which group addresses communicate securely and which group addresses communicate conventionally.
Furthermore, it can also have mixed operation of Secure and plain(conventional) communication on a sensor or actuator via different communication objects.
However, secured and unsecured communication via one and the same communication object is not possible. The ETS project determines which group addresses communicate securely and which group addresses communicate conventionally.

Q5
What is required for system components e.g. line coupler for used in KNX Data Secure installation?
Ans
The system components including coupler and (USB) interface must support Extended because the longer telegram format used by KNX Data Secure. This must always be considered when communicating between lines and especially when existing KNX installations are extended with KNX Data Secure. It may be necessary to replace older system components with components compatible with KNX Data Secure.
Q6
Is it possible to disable the secure function from a KNX Data Secure device?
Ans
Yes device with KNX Data Secure can also be configured with the ETS in a traditional manner which means it communicate with unsecured or plain telegrams at runtime for daily operation.
The behavior is same as for device without KNX Data Secure. It means that KNX Data Secure device can also be used in existing system to replace defective unit e.g. actuator.
It is not required to modify the entire KNX system or parts of it, or to update it to secure communication. The system integrator just need to set the Secure Commissioning to “Deactivated” in the application database of KNX Data Secure device shown in the picture below.
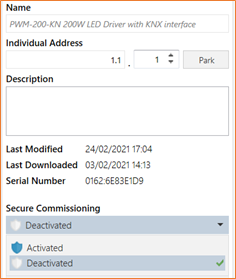
The behavior is same as for device without KNX Data Secure. It means that KNX Data Secure device can also be used in existing system to replace defective unit e.g. actuator.
It is not required to modify the entire KNX system or parts of it, or to update it to secure communication. The system integrator just need to set the Secure Commissioning to “Deactivated” in the application database of KNX Data Secure device shown in the picture below.

Q7
Why KNX Data Secure has same speed as plain one?
Ans
A KNX Data Secure telegram encrypts only the data protocol information (APCI) and the payload (data) while telegram header, source and destination address are transmitted with signature in plain text. This has the advantage that Data Secure telegrams do not require decryption for telegram routing through area/line couplers or media couplers. It is therefore media-neutral and does not affect the transaction speed of transmitted telegrams as compared to plain communication.
Q8
How does the KNX Data Secure work?
Ans
The KNX Data Secure mechanism can be divided into four parts which is individually explained in the following:
- Freshness
It prevents an intruder from recording permissible telegrams at any time and replaying them again later. For example, the intruder would like to open a garage door via an illegally recorded 1-bit switching command. A (KNX Data Secure device) receiver only accepts "fresh" telegrams from a sender.
Freshness is realized via a 6-byte long transmission sequence number. A KNX secure receiver device, e.g. actuator, only evaluates a group telegram as valid if the contained sequence number from sender, e.g. pushbutton sensor, is at least one value higher than the last received value of the same sender. Telegrams that have a lower or the same value are rejected by the receiver.
The transmission sequence number do not always have to be exactly one value higher (n+1). It is important that the number is continuous (n+x). During a master reset, the transmission sequence number is automatically reset to an initial value. When replacing a device, the ETS attempts to detect reset devices and replaces the initial value with a valid transmission sequence number using a predefined method.
During a programming procedure, separate sequence numbers are used by the ETS and the device. Transmission sequence numbers can be viewed in the group monitor of the ETS. They are not encrypted but protected against manipulation.
Freshness is realized via a 6-byte long transmission sequence number. A KNX secure receiver device, e.g. actuator, only evaluates a group telegram as valid if the contained sequence number from sender, e.g. pushbutton sensor, is at least one value higher than the last received value of the same sender. Telegrams that have a lower or the same value are rejected by the receiver.
The transmission sequence number do not always have to be exactly one value higher (n+1). It is important that the number is continuous (n+x). During a master reset, the transmission sequence number is automatically reset to an initial value. When replacing a device, the ETS attempts to detect reset devices and replaces the initial value with a valid transmission sequence number using a predefined method.
During a programming procedure, separate sequence numbers are used by the ETS and the device. Transmission sequence numbers can be viewed in the group monitor of the ETS. They are not encrypted but protected against manipulation.
- Confidentiality
The telegram confidentiality prevents the reading of telegrams by means of encryption. This means that intruder no longer has access to KNX installation data transmitted e.g. Light ON/OFF, without having the group or ETS keys.
128-bit AES encryption algorithm with symmetric keys are used to encrypt telegrams. A symmetric key means that the same key is used both by the sender to encrypt outgoing messages (authentication and integrity protection) and by the recipient(s) to verify and decrypt the received messages.
128-bit AES encryption algorithm with symmetric keys are used to encrypt telegrams. A symmetric key means that the same key is used both by the sender to encrypt outgoing messages (authentication and integrity protection) and by the recipient(s) to verify and decrypt the received messages.
- Data integrity
Data integrity effectively prevents an intruder from obtaining control over a KNX system. It prevents telegrams from being manipulated or added additional (incorrect) information. This is done by inserting an encrypted authentication code into each telegram. Recipients can use this code to verify whether a message has been illegally modified.
KNX Data Secure uses the CBC-MAC-Mode with AES encryption included in CCM mode to ensure data integrity. A "Message Authentication Code" (MAC) is attached to the message. This authentication code signs all information contained in the telegram so that manipulation can be detected.
KNX Data Secure uses the CBC-MAC-Mode with AES encryption included in CCM mode to ensure data integrity. A "Message Authentication Code" (MAC) is attached to the message. This authentication code signs all information contained in the telegram so that manipulation can be detected.
- Authentication
Authentication is used to verify the identity of the telegram. It ensures that the source of a telegram is indeed an authorized communication partner. A receiver rejects a received commissioning or group telegram if the source address (physical address) of the telegram is unknown.
The identity of a received telegram is verified via the contained physical address of the sender (source address). A recipient only authorizes the telegram if the source address contained was entered in a special communication table which is automatically programmed by the ETS during commissioning. The table contains a combination of the physical addresses of the permitted communication partners and their transmission sequence numbers in list.
The identity of a received telegram is verified via the contained physical address of the sender (source address). A recipient only authorizes the telegram if the source address contained was entered in a special communication table which is automatically programmed by the ETS during commissioning. The table contains a combination of the physical addresses of the permitted communication partners and their transmission sequence numbers in list.
Q9
What is device certificate?
Ans
The device certificate is a string with 36 characters containing the FSDK and the KNX serial number of a KNX Data Secure device. The device certificate should be first read-in by ETS before the commissioning in order to be able to activate the Data Secure on a device.
The device certificate is printed on removable label attached to the device. The label must be removed from the device after mounting and stored safely to prevent that unauthorised person obtains the FDSK and manipulate existing device of a secure KNX installation.
The QR code contains the device certificate in machine-readable form and can be read into a ETS project via a webcam without typing-in.

The device certificate is printed on removable label attached to the device. The label must be removed from the device after mounting and stored safely to prevent that unauthorised person obtains the FDSK and manipulate existing device of a secure KNX installation.
The QR code contains the device certificate in machine-readable form and can be read into a ETS project via a webcam without typing-in.

Q10
What is FDSK?
Ans
The Factory-Default-Setup-Key (FDSK) is used for the first time commissioning of a KNX Data Secure device with ETS. The FDSK already becomes invalid during the initial secure commissioning when writing the physical address and is replaced by the so-called Toolkey generated by ETS.
The FDSK is 128-bit long and represents the manufacturer's initial key of a KNX Data Secure device. The FDSK is included in the device certificate which is attached to the device upon delivery.
Providing the FDSK has been successfully read in during initial commissioning, it is archived in a readable form in the ETS project together with the device certificates. It can be restored by a master reset of the device and consequently reactivated so that the device can be recommissioned as complete new device. If the device certificate attached to the devices and consequently the FDSK is lost, a device can no longer be securely commissioned by other ETS projects. However it can still be commissioned as traditional KNX device without Data Secure. Should you need a lost FDSK, contact the manufacturer for details.
The FDSK is 128-bit long and represents the manufacturer's initial key of a KNX Data Secure device. The FDSK is included in the device certificate which is attached to the device upon delivery.
Providing the FDSK has been successfully read in during initial commissioning, it is archived in a readable form in the ETS project together with the device certificates. It can be restored by a master reset of the device and consequently reactivated so that the device can be recommissioned as complete new device. If the device certificate attached to the devices and consequently the FDSK is lost, a device can no longer be securely commissioned by other ETS projects. However it can still be commissioned as traditional KNX device without Data Secure. Should you need a lost FDSK, contact the manufacturer for details.
Q11
What is Master Reset?
Ans
The master reset is a function for resetting a KNX Data Secure device to a factory default state defined by the manufacturer. When executing a master reset, the physical address is initialized to 15.15.255, all RuntimeKey and the Toolkey are deleted and FDSK(device certificate) is active again for recommissioning with the ETS.
The firmware of a device is not affected by a master reset. Triggering and signalling of the master reset is device-specific and is explained in the respective product documentation.
All Mean Well KNX Data Secure products can be reset by long-press PROG button > 10 seconds.
The firmware of a device is not affected by a master reset. Triggering and signalling of the master reset is device-specific and is explained in the respective product documentation.
All Mean Well KNX Data Secure products can be reset by long-press PROG button > 10 seconds.
Q12
What is Toolkey?
Ans
The Toolkey is exclusively used by the ETS to program a KNX Data Secure device. It is 128-bit long, unique for one device in the project and replaces the FDSK already upon initial commissioning. The ETS then uses the Toolkey for each programming procedure in secure mode. Without the Toolkey, e.g. access via other ETS projects, a securely commissioned device can only be reprogrammed if Master Reset is executed.
The Toolkey is archived in the ETS project in unreadable form for the ETS user because it is only relevant for ETS in the existing project. If the project is exported, the ETS writes all Toolkeys of the project in an encrypted and signed form to the *.KNXPROJ file.
The Toolkey is archived in the ETS project in unreadable form for the ETS user because it is only relevant for ETS in the existing project. If the project is exported, the ETS writes all Toolkeys of the project in an encrypted and signed form to the *.KNXPROJ file.
Q13
What is RuntimeKey?
Ans
The RuntimeKey or GroupKey is the AES key for group address communication at runtime. In an ETS project, each group address has its own 128-bit long RuntimeKey, provided the address is used for secure communication between KNX Data Secure devices. As with the Toolkey, the RuntimeKeys are archived in unreadable form for ETS users in the ETS project and are written to the project file in a protected form when exporting the project.
If required, all or selected RuntimeKeys of an existing project can be exported to a special password-protected export file (*.knxkeys), also known as a project keyring. This export is required if components are to interact with a KNX Data Secure system, but are not configured and commissioned with the ETS (e.g. visualizations). In such cases, the ETS can be used to export a runtime keyring.
If required, all or selected RuntimeKeys of an existing project can be exported to a special password-protected export file (*.knxkeys), also known as a project keyring. This export is required if components are to interact with a KNX Data Secure system, but are not configured and commissioned with the ETS (e.g. visualizations). In such cases, the ETS can be used to export a runtime keyring.
Q14
What is KNX Serial Number?
Ans
The KNX serial number is a 6-byte long identification number of the manufacturer for unique identification on each KNX device. The serial number is programmed into the device during production and not re-writable during runtime.
The ETS uses the serial numbers to identify new and already commissioned devices in a KNX installation. The serial numbers of all read-in device certificates in the project and of all commissioned devices are archived by the ETS in the project keyring.

The ETS uses the serial numbers to identify new and already commissioned devices in a KNX installation. The serial numbers of all read-in device certificates in the project and of all commissioned devices are archived by the ETS in the project keyring.

